شرکت مایکروسافت در آخرین پژوهشنامه خود اعلام کرد که (CVE-2018-5483) به عنوان یک حفره امنیتی در بخش win32k.sys وجود داشت که توسط کارشناسان شرکت کسپرسکی در ماه اوت شناسایی و به آن شرکت اعلام گردید. شرکت مایکروسافت در تاریخ 17 اوت این مطلب تائید کرده و تلاش خود را برای بر طرف کردن آن آغاز نمود و طبق کد گذاری خود کد CVE-2018-5483 را به این حفره امنیتی اختصاص داد.
در اوت سال 2018 سیستم خودکار پیشگیری از نفوذ کسپرسکی (AEP) وجود یک حفره امنیتی در سیستم عامل ویندوز را تشخیص داد. در بررسی های بیشتر مشخص شد که این نقص درون win32k.sys قرار دارد. با ورود از طریق این حفره امنیتی یک بد افزار قادر خواهد بود پس از نصب خود دسترسی را تا سطح بالایی افزایش دهد و از حداکثر منابع به راحتی سو استفاده کند. تعداد کمی از حملات کشف شده از این طریق نشان می دهد که اکثر قربانیان در خاورمیانه قرار دارند.
شرکت کسپرسکی این نقص امنیتی را از طریق راه های زیر تشخیص داده است:
- موتور شناسایی رفتار و جلوگیری از نفوذ خودکار بر روی کلاینت ها
- استفاده از سندباکس پیشرفته و قابلیت ضد تروجان در Kaspersky KATA
جهت دریافت آپدیت های مورد نظر به سایت مایکروسافت مراجعه کنید. [divider height=’65’]
اطلاعات فنی بیشتر
[divider height=’30’]
CVE-2018-8453 is a Use-After-Free inside win32kfull!xxxDestroyWindow that resembles an older vulnerability — CVE-2017-0263. CVE-2017-0263 was originally deployed by the Sofacy APT, together with a PostScript exploit, back in 2017.
For technical analysis of the vulnerability, we completely reverse-engineered the ITW exploit sample obtained and rewrote it into a full Proof of Concept.
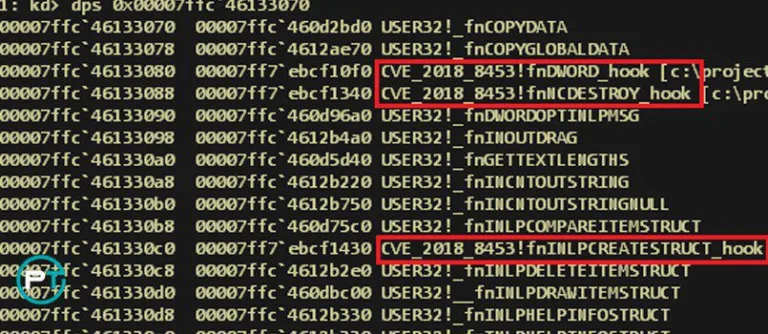
The exploitation of this vulnerability depends on a sequence of events that are performed from hooks set on three usermode callback functions – fnDWORD, fnNCDESTROY, and fnINLPCREATESTRUCT. The exploit installs these hooks by replacing the function pointers in the KernelCallbackTable:
Hooked functions in the Kernel Callback Table
Inside the fnINLPCREATESTRUCT hook, the exploit initializes a “SysShadow” window by explicitly assigning a position to it:
Usermode hook on fnINLPCREATESTRUCT initializes SysShadow
When processing the WM_LBUTTONDOWN message, the fnDWORD hook executes the DestroyWindow function on the parent, which results in the window being marked as free and subsequently freed by the garbage collector.
The issue lies inside the fnNCDESTROY hook that is performed during execution of the DestroyWindow function. This hook executes the NtUserSetWindowFNID syscall, which contains a flawed logic to change the fnid status of the window without properly checking if it is set to FNID_FREED.
Vulnerable code inside NtUserSetWindowFNID
The fnid status of the window is located at offset 0x02a in the tagWND structure:
kd> dt win32k!tagWND
…
+0x02a fnid : Uint2B
When the scrollbar is initially created, it has the value FNID_SCROLLBAR (0x029A).
The next diagram shows the value of fnid prior and after execution of the NtUserSetWindowFNID syscall:
Scrollbar fnid prior and after execution of NtUserSetWindowFNID syscall
We can check what the new fnid value is by verifying it against the ReactOS source code:
/* FNIDs for NtUserSetWindowFNID, NtUserMessageCall */
#define FNID_SCROLLBAR 0x029A
…
#define FNID_BUTTON 0x02A1
…
#define FNID_FREED 0x8000 /* Window being Freed… */
This action results in the first scrollbar being destroyed, while the system still maintains a reference to a “SysShadow” class, as the scrollbar fnid is no longer marked as FNID_FREED, but as FNID_BUTTON instead.
To successfully reclaim the freed memory pool, the exploit contains a number of different feng shui tactics. The spray procedure is dependent on the exploited Windows version, and because the exploit targets a wide range of operating systems, it includes five separate functions for spraying:
Heap spraying procedures supported in the exploit
For the latest supported version (Windows 10 RS4), the spray tactic is quite complicated. The kernel is sprayed with bitmap objects of different size. This is required to exhaust the memory allocator to eventually bypass the Low Fragmentation Heap security mitigations that were significantly improved in the latest Windows builds:
Heap Feng Shui technique for Windows RS4 17134
This leads to the following memory layout, where USERTAG_SCROLLTRACK is the freed pool allocation:

Freed scrollbar heap allocation
When another scrollbar is allocated, the SysShadow class memory reference is reused, but its contents are attacker-controlled, because the freed Usst (ffffee30044b2a10) and Gpbm (ffffee30044b2a90) pools were merged into a single block:
Freed allocation is merged with the following pool
This results in a powerful arbitrary kernel Read\Write using GDI Bitmap primitives that works even on the latest Windows versions.
Following successful exploitation, a slightly modified Token-stealing payload is used to swap the current process Token value with the one from the SYSTEM EPROCESS structure:
Modified Token-stealing payload process
So far, we’ve observed the usage of this exploit in a small number of targeted attacks, when the exploit is packaged in a malware installer. The installer requires system privileges to install its payload. The payload is a sophisticated implant, used by the attackers for persistent access to the victims’ machines. Some of its main characteristics include:
- Encrypting the main payload using AES-256-CBC with the SHA-1 of the SMBIOS UUID (this makes it impossible to decrypt the payload on machines other than the victim, if the SMBIOS UUID is not known)
- Using Microsoft BITS (Background Intelligent Transfer Service) for communicating with its C&C servers, an unusual technique
- Storing the main payload in a randomly named file on disk; the loader contains a hash of the filename and attempts to find the payload by comparing the filename hash for all files in the Windows directory
منبع: Kaspersky